Setting up Network Encryption in our Oracle environment is very easy, we just need to add these lines to the sqlnet.ora on server side:
[root@dune ~]# cat /u01/app/oracle/product/19c/db_1/network/admin/sqlnet.ora
# sqlnet.ora Network Configuration File: /u01/app/oracle/product/19c/db_1/network/admin/sqlnet.ora
# Generated by Oracle configuration tools.
NAMES.DIRECTORY_PATH= (TNSNAMES, ONAMES, HOSTNAME)
SQLNET.ENCRYPTION_SERVER = REQUIRED
SQLNET.ENCRYPTION_TYPES_SERVER = (AES256)
SQLNET.CRYPTO_CHECKSUM_SERVER = REQUIRED
SQLNET.CRYPTO_CHECKSUM_TYPES_SERVER = (SHA512)
[root@dune ~]#Ideally, on the client side we should add these too:
SQLNET.ENCRYPTION_CLIENT = REQUESTED
SQLNET.ENCRYPTION_TYPES_CLIENT = (AES256)
SQLNET.CRYPTO_CHECKSUM_CLIENT = REQUESTED
SQLNET.CRYPTO_CHECKSUM_TYPES_CLIENT = (SHA512)
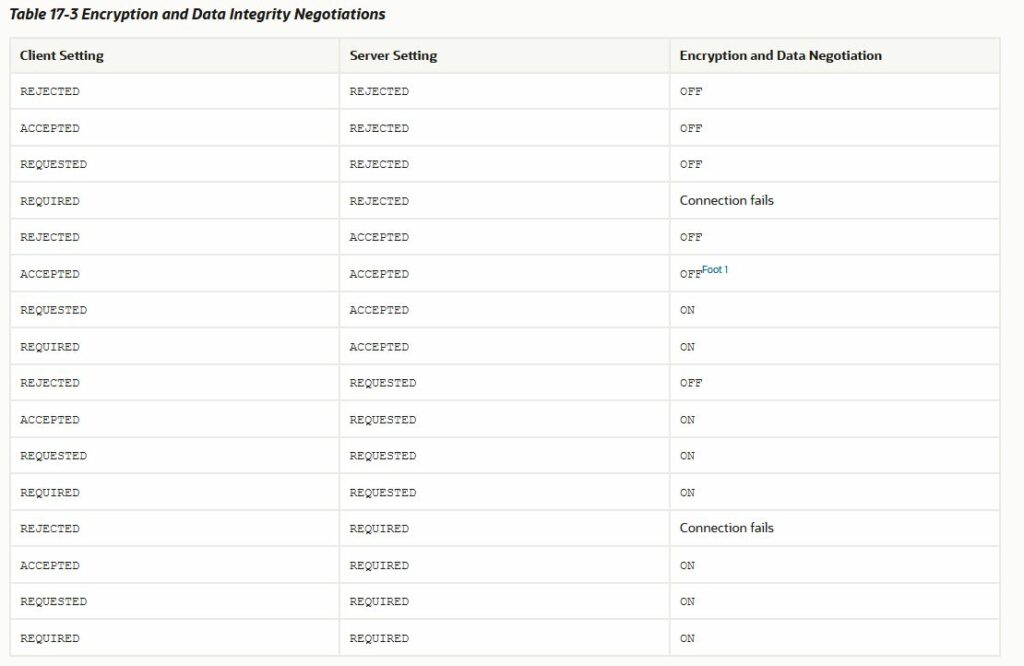
But since ENCRYPTION_CLIENT by default is ACCEPTED, if we see this chart, connection would be encrypted (ACCEPTED – REQUESTED case)
Lets connect to the DB and see if comminutation is encrypted:
[oracle@athena ~]$ sqlplus dbsnmp@testdb
...
Enter password:
Last Successful login time: Tue Mar 22 2022 13:58:44 +00:00
Connected to:
Oracle Database 19c Enterprise Edition Release 19.0.0.0.0 - Production
Version 19.13.0.0.0
SQL>
SQL> select network_service_banner
from v$session_connect_info
where sid in (select distinct sid from v$mystat); 2 3
NETWORK_SERVICE_BANNER
--------------------------------------------------------------------------------
TCP/IP NT Protocol Adapter for Linux: Version 19.0.0.0.0 - Production
Encryption service for Linux: Version 19.0.1.0.0 - Production
AES256 Encryption service adapter for Linux: Version 19.0.1.0.0 - Production
Crypto-checksumming service for Linux: Version 19.0.1.0.0 - Production
SHA512 Crypto-checksumming service adapter for Linux: Version 19.0.1.0.0 - Produ
ction
SQL>
Here we can see AES256 and SHA512 and indicates communication is encrypted.
Now lets see what happens at package level, first lets try without encryption.
Lets start capturing packages on target server (client is 192.168.56.121):
[root@dune ~]# tshark -i enp0s10 host 192.168.56.121 -x
Execute query (connecting from remote server)
[oracle@athena ~]$ tnsping testdb
...
Attempting to contact (DESCRIPTION = (ADDRESS_LIST = (ADDRESS = (PROTOCOL = TCP)(HOST = dune.localdomain)(PORT = 1522))) (CONNECT_DATA = (SERVICE_NAME = testdb)))
OK (0 msec)
[oracle@athena ~]$
SQL> select INSTANCE_NAME, STATUS from v$instance;
INSTANCE_NAME STATUS
---------------- ------------
testdb OPEN
This is how wireshark sees the packages, plain text:
0150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0170 00 00 00 00 00 00 2d 20 73 65 6c 65 63 74 20 49 ......- select I
0180 4e 53 54 41 4e 43 45 5f 4e 41 4d 45 2c 20 53 54 NSTANCE_NAME, ST
0190 41 54 55 53 20 66 72 6f 6d 20 76 24 69 6e 73 74 ATUS from v$inst
01a0 61 6e 63 65 01 00 00 00 00 00 00 00 00 00 00 00 ance............
...
...
0140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0160 00 00 07 06 74 65 73 74 64 62 04 4f 50 45 4e 08 ....testdb.OPEN.
0170 06 00 60 9f 5e 00 00 00 00 00 03 00 00 00 00 00 ..`.^...........
As we can see, comunicaitons are in plain text.
Now lest try with Native Network Encryption enabled and execute the same query:
[root@dune ~]# tshark -i enp0s10 host 192.168.56.121 -x
...
0180 71 3e 5d 89 b9 57 43 ac 29 4b f4 5e 97 b5 84 a8 q>]..WC.)K.^....
0190 9c a5 3f c2 87 a2 08 76 dc 50 2b a0 79 33 dc 8c ..?....v.P+.y3..
01a0 18 54 46 de 18 28 7c c0 3f 5c 3d fa 17 1a 72 12 .TF..(|.?\=...r.
01b0 28 d9 14 7a 24 15 39 11 9e c2 05 53 0a 9f 50 05 (..z$.9....S..P.
01c0 2c f8 f8 f0 4d ee eb 2b cb 64 91 7b 04 9f 06 cd ,...M..+.d.{....
01d0 fd 2b be b5 c4 f4 73 8d ac 83 1c 37 b4 cf 60 43 .+....s....7..`C
01e0 d1 b1 16 ae 59 02 c8 77 7e 6b ab a6 e0 64 58 40 ....Y..w~k...dX@
01f0 16 c9 79 b9 d0 63 fc 51 a6 e9 1d e2 91 d5 53 4e ..y..c.Q......SN
0200 2b 29 54 87 37 67 df 42 f5 be 9d 9b df 93 d6 ec +)T.7g.B........
0210 86 28 96 32 61 df 64 2b 1c f7 31 86 78 35 97 f7 .(.2a.d+..1.x5..
0220 fc cf 3b 21 20 7a 82 0a 2b 8a 54 b5 f3 77 39 98 ..;! z..+.T..w9.
0230 18 ed bf 9f 69 1f 3c 1f e6 f1 0f 1b 8a 9d 4e 29 ....i.<.......N)
0240 cc 19 3e 1f 71 60 91 99 10 b3 63 2f 06 01 ..>.q`....c/..
We can see the packages are now encrypted.
Comments